Implementing over-the-air updates for IoT devices
September 08, 2025When people think of connected devices, they often imagine convenience and automation. But behind every smart thermostat, industrial sensor, or connected car lies a critical challenge: how do you keep these devices secure, functional, and up-to-date once they’re deployed in the field? The answer is over-the-air (OTA) updates. OTA updates enable manufacturers and operators to deliver new firmware, security patches, or configuration changes without physically touching the device.
This has gone from a “nice-to-have” to a mission-critical requirement. For example, Tesla famously deploys software updates remotely that improve vehicle performance, fix bugs, and even add new features, avoiding costly recalls and dealership visits. The scale of the challenge is enormous. By 2030, the number of IoT devices is projected to reach 29.4 billion worldwide, according to Statista. Managing updates manually is simply impossible. Without OTA, entire fleets of devices would quickly become insecure, obsolete, or non-compliant.
What are OTA updates and why do they matter
An OTA update is the wireless delivery of new software or firmware to connected devices. Instead of technicians plugging in USB drives or connecting laptops on-site, devices receive updates through the internet or other networks. Compared to manual updates, OTA is faster, cheaper, and safer. For example, a utility company managing 100,000 smart meters can’t afford to send technicians into the field every time a firmware bug is found. OTA eliminates this bottleneck.
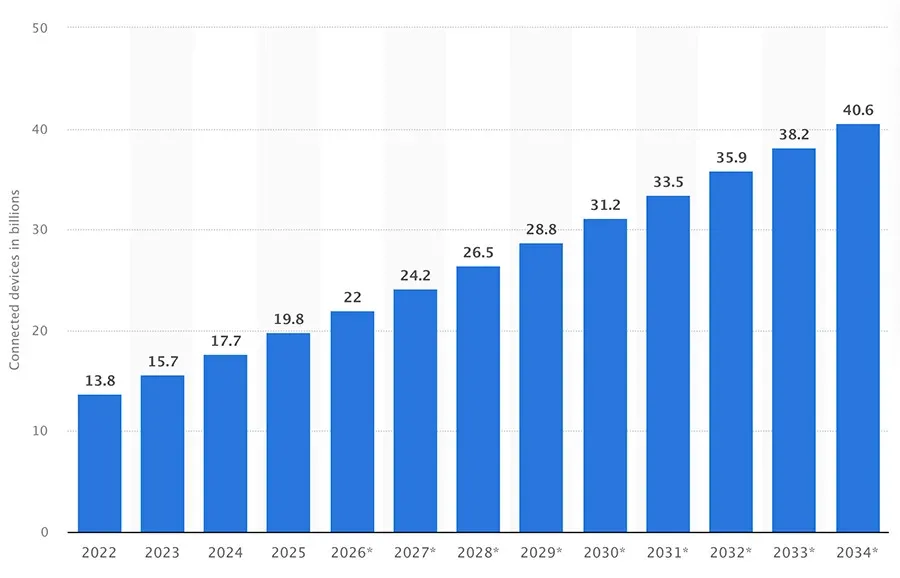
Number of Internet of Things (IoT) connections worldwide from 2022 to 2023, with forecasts from 2024 to 2034
The key drivers for OTA adoption are:
- security
- cost reduction;
- scalability and compliance.
Threats evolve daily, and unpatched firmware leaves devices susceptible to vulnerabilities. Remote updates eliminate the need for costly site visits, resulting in significant cost savings. Manufacturers can update millions of devices at once. Certain industries (like healthcare and automotive) require strict update processes. Take medical wearables: a manufacturer might discover a flaw in the way devices record patient data. Instead of recalling thousands of units, OTA enables the company to push a fix overnight.
Key components of an OTA update system
Implementing OTA isn’t just about sending files. It requires a structured system where each component plays a role.
- Update server – central repository storing firmware images, managing versions, and distributing updates.
- Device agent – lightweight client installed on each device, responsible for checking, downloading, and applying updates.
- Secure communication channel – protocols like HTTPS or MQTT over TLS ensure data is encrypted and authenticated.
- Management console – a dashboard where administrators schedule, monitor, and analyze update campaigns.
In practice, these elements form a feedback loop. The server sends updates, the device agent executes them, and telemetry flows back to confirm success or failure. So, let's take a look at the core requirements for OTA systems:
- Secure authentication and encryption – prevent tampering during transmission.
- Delta updates – deliver only the changes, reducing bandwidth and cost.
- Rollback capabilities – revert to the previous version if an update fails.
- Version management – track firmware across diverse fleets.
- Remote monitoring – verify update success rates and catch anomalies.
Security considerations in OTA updates
OTA introduces a paradox: the same connectivity that enables remote updates also opens the door to attackers. Without proper safeguards, malicious actors could push fake firmware, compromise devices, or even hijack entire fleets. The most common risks include man-in-the-middle (MITM) attacks that intercept update traffic; unsigned firmware that is being installed on devices and replay attacks where old, vulnerable firmware is reintroduced. To mitigate these risks: secure boot ensures only signed firmware is executed. Code signing uses digital signatures to verify authenticity. Public Key Infrastructure (PKI) provides device identity and trust chains.
The consequences of neglect are clear. The Mirai botnet, which in 2016 weaponized insecure IoT devices, was largely possible because devices shipped with outdated or weakly protected firmware. Today, those risks are amplified by billions of endpoints. A recent study confirms the stakes: 43% of IoT device breaches in 2023 were attributed to unpatched vulnerabilities. OTA systems with robust security are the only defense against this reality.
Implementation strategies: step-by-step
Rolling out OTA updates successfully requires more than a server and a few scripts. Here’s a structured approach:
- Step 1: Choose an OTA framework. Options include commercial platforms, open-source solutions, and dedicated platforms like the Kaa IoT Platform.
- Step 2: Prepare firmware packages. Optimize for size (use delta updates), compress when possible, and always sign with cryptographic keys.
- Step 3: Secure the delivery pipeline. Use TLS/DTLS encryption, device authentication, and strict access controls.
- Step 4: Test in staging. Simulate rollouts in controlled environments with diverse device profiles.
- Step 5: Rollout strategy. Deploy updates gradually: start with a small percentage (canary group), then expand if successful.
- Step 6: Monitor and log results. Track metrics such as update success rate, failure reasons, device downtime, and bandwidth utilization.
Also, let's consider common pitfalls to avoid. The first one is pushing updates to all devices at once and can brick fleets if something goes wrong. The second – ignoring low-bandwidth environments – some devices can’t handle large payloads. Skipping rollback options is another pitfall – a failed update may disable mission-critical equipment. Also, overlooking compliance rules wont be a good idea – industries like healthcare (FDA) or automotive (ISO 26262) have strict OTA requirements.
Best practices for scaling OTA across fleets
Managing a handful of devices is easy, but scaling to hundreds of thousands across different geographies requires a strategic approach. Successful deployments begin with proper segmentation: organizing devices by location, hardware version, or use case to avoid blanket rollouts that could overwhelm systems or create unnecessary risk. Automation is equally critical. By using a rules engine, operators can define when, how, and which devices receive updates, reducing manual oversight while ensuring updates happen under the right conditions. Monitoring also plays a major role at scale: update success rates, bandwidth usage, and device health after each deployment provide the feedback loop needed to keep operations running smoothly.
Equally important is regulatory compliance, which varies by industry. Medical IoT devices, for example, must adhere to FDA requirements for software updates, while automotive manufacturers need to follow ISO 26262 safety standards. As fleets grow, emerging technologies such as AI-assisted OTA add another layer of efficiency. Machine learning can predict the best update windows, automatically schedule rollouts during low-usage periods, and detect anomalies in real time. Ultimately, the guiding principle is to view OTA not as a one-off maintenance task, but as a continuous lifecycle management tool that ensures devices remain secure, reliable, and compliant throughout their entire operational lifespan.
Conclusion
Over-the-air updates are no longer optional. They’re the backbone of maintaining IoT fleets securely, efficiently, and at scale. Without OTA, connected devices quickly become liabilities: exposed to hackers, prone to failure, and expensive to maintain. The benefits are tangible: reduced downtime, lower costs, improved compliance, and increased customer satisfaction. OTA also transforms IoT devices from static hardware into living, evolving platforms. In a world heading toward 30 billion connected devices, the companies that master OTA will not only survive but lead, delivering secure, reliable, and continuously improving IoT experiences.





