IoT Data Storage: Threats with Solutions
March 20, 2024As the Internet of Things (IoT) expands its reach across industries, the importance of reliable and adaptable storage solutions for IoT data grows significantly. The diverse data generated by IoT devices, including sensor readings and videos, calls for strong storage systems capable of managing this range effectively. In this landscape, IoT data storage solutions are essential for gathering, analyzing, and preserving data from smart devices, empowering organizations to discover valuable insights and make informed decisions. This article delves into different IoT data storage options, shedding light on their features, obstacles, and security considerations.
IoT data storage segments
IoT data storage refers to capturing, managing, and storing the data generated by IoT devices. These devices, ranging from sensors and actuators to smartphones and wearables, continuously produce data streams containing valuable insights about the physical world. IoT data storage solutions are drafted to efficiently handle this diverse and often unstructured data, ensuring its integrity, availability, and accessibility for analysis and decision-making purposes.
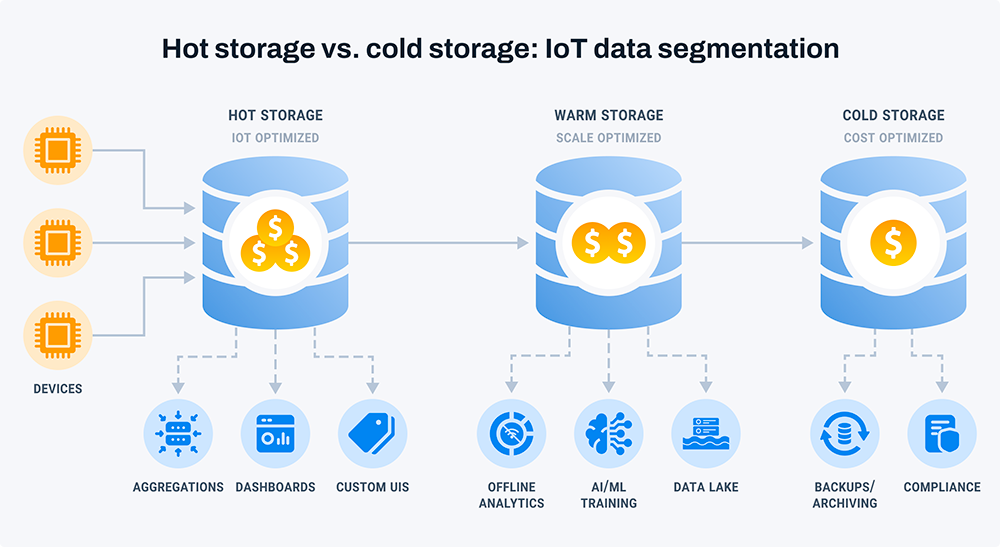
When managing large-scale operations, it is crucial to categorize data and use storage technology tailored to each segment. IoT data storage has three segments:
Hot storage
A hot storage database powers the front end of your IoT application, ensuring fast access to data for immediate querying and display on user interfaces. IoT devices mainly generate time-series data, and a well-designed hot storage database is tailored for time-based aggregations like minimum, maximum, mean, and standard deviation.
Managing the high-performance demands of a hot storage database comes at a high cost. Most hot storage setups incorporate data retention policies to manage costs. It means that data remains in the hot storage database for a set period before being removed.
Warm storage
Warm storage is a data storage that sits between hot storage (which prioritizes fast access and real-time querying) and cold storage (which focuses on long-term retention at a lower cost). Warm storage typically retains data that is not actively accessed but may still be needed for analysis or historical reference. It provides a balance of performance and cost-effectiveness, offering relatively faster access times compared to cold storage while being more economical than hot storage. Warm storage is used for storing data accessed occasionally or intermittently, serving as an intermediate tier in a data storage hierarchy.
Cold storage
Cold storage is data storage optimized for long-term data retention at a low cost. Different from hot storage, which prioritizes fast access and real-time querying, cold storage is designed for infrequently accessed or rarely modified data. It typically offers slower retrieval times compared to hot storage but is more cost-effective for storing large volumes of data over extended periods. Cold storage solutions often utilize technologies such as magnetic tape or object storage systems with lower performance requirements but higher scalability and durability. Cold storage is commonly used for archival data, backups, regulatory compliance, and disaster recovery purposes.
Four aspects of storing IoT data
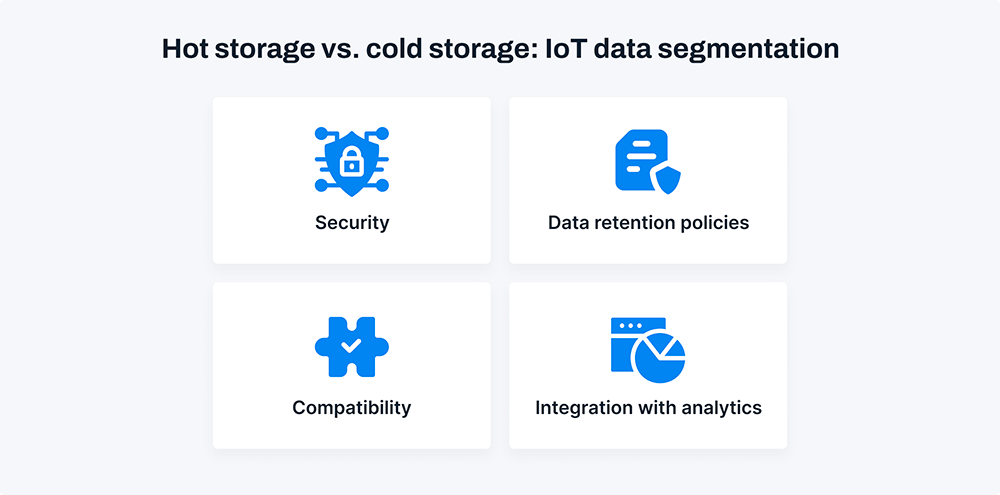
Security
Security in IoT data storage is to protect the sensitive information collected by IoT devices. This involves encrypting data both at rest and in transit, implementing strong access controls, ensuring data integrity, using secure communication protocols, selecting secure storage solutions, conducting regular audits and monitoring, and following secure development practices. These measures help mitigate the risk of data breaches and unauthorized access, ensuring the confidentiality and integrity of IoT data.
Data retention policies
Data retention policies refer to guidelines and protocols for managing the lifespan of stored data. These policies dictate how long data should be retained when it should be archived or deleted, and under what circumstances it can be accessed or modified. Data retention policies typically consider factors such as regulatory requirements, business needs, data usage patterns, and privacy considerations. They help organizations optimize storage resources, ensure compliance with relevant regulations, mitigate security risks, and maintain data integrity.
Compatibility
Compatibility refers to how well storage systems and protocols can smoothly interact with different IoT devices, apps, and platforms. It guarantees that data can move, be stored, and accessed effectively across diverse hardware and software setups without running into issues or format clashes. Key compatibility factors involve making sure IoT devices can work together with storage systems, supporting standard communication protocols, and following common data formats and standards.
Integration with analytics
Integrating analytics with IoT data storage is like linking storage systems with tools that help uncover insights from IoT data. This connection empowers organizations to use advanced analytics such as machine learning, predictive modeling, and real-time analysis to gain valuable insights and make informed decisions using data from IoT devices. IoT data storage solutions are key in managing, transforming, and analyzing large amounts of data from IoT devices. This ability helps organizations discover important patterns, trends, anomalies, and connections that can boost operations, streamline processes, enhance customer experiences, and open up new business possibilities.
Data security threats for IoT data storage
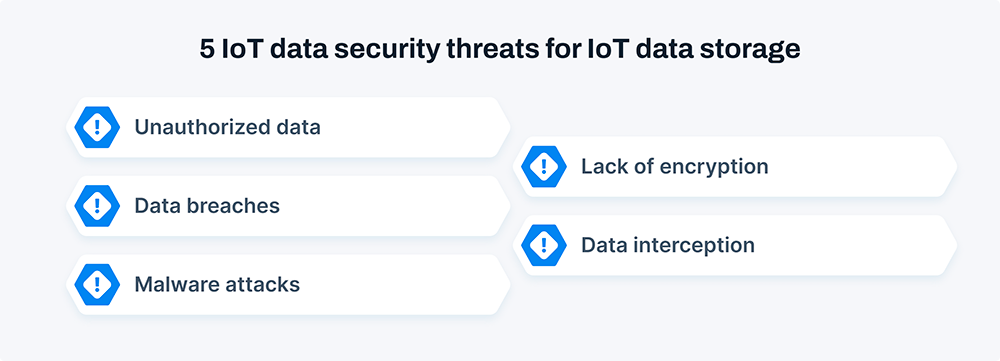
Unauthorized access
Unauthorized access occurs when someone gains entry to a system, application, or data without permission. In IoT data storage, this unauthorized access happens when individuals or entities get into stored IoT data without the right authorization. It can happen through different methods like exploiting system vulnerabilities, guessing or stealing login details, or circumventing security measures.
Unauthorized access to IoT data can result in severe outcomes, such as data breaches, theft of sensitive information, and compromising system integrity. This breach can lead to financial losses, harm to reputation, and legal consequences for organizations accountable for safeguarding the data.
Data breaches
The fact that data breaches ensue as a result of unauthorized persons/entities inorganically tapping the company databases or systems is a real problem. These incidents can be through a multitude of ways, like cyber attacks, insider threat, etc. Human error or vulnerabilities of the systems or software could also be the source of these breaches.
Data breaches, even marginal, can devastate their victim and lead to monetary losses, tarnishing corporate reputation, lawsuits, and personal data disclosure. The consequences of the breach can be very different if personal data is exposed. Individuals who have been affected may be at high risk of being victims of identity theft, fraud or other malpractice.
Malware attacks
Malware attacks are carried out by means of introducing malicious software that aims at violating the system, deceiving users or inflicting loss on devices and networks. The types of malware include viruses and worms which perform different tasks; trojans; ransomware; spyware, or advertising malware which also have different objectives.
With regards to IoT data storage, malware threats may be the source of substantial risks for the security and integrity of stockpiled data. Hackers can penetrate IoT by utilizing malware to breach the devices, exploit the vulnerabilities in firmware or software codes or loopholes in the networks that leads to inaccessible data.
Lack of encryption
The lack of cryptography is associated with the absence of security in regard to personal information encryption both during the transfer and storage, which leads to interception and unauthorized access to the data. This vulnerability arises when data is saved or transferred without encryption method on the field. It is when the data appears in in plain text which can be accessed or read by unauthorized parties.
The encrypting cannot get a clearer picture than what is missing if the data stored on devices is not encrypted or transmitted over networks, enabling malicious actors to intercept them easily so as to disclose it to the world and take their data integrity and confidentiality away. This vulnerability is quite high when it comes to IoT where data is transmitted wirelessly, either over public or unsecured networks, consequently, opens a possibility for eavesdroppers or hackers where they can get to the data.
Data interception
Data interception refers to the unauthorized capture or monitoring of transmitted data over a network or communication channel. IoT data storage interception poses a significant security threat when sensitive information is transmitted between IoT devices, gateways, and cloud-based storage systems.
Malicious actors can intercept IoT data by exploiting vulnerabilities in network protocols, wireless communication channels, or infrastructure components such as routers and gateways. After the interception, the data can be captured, monitored, or tampered with without the permission or awareness of the rightful data owners or authorized users.
IoT four data storage solutions
IoT data storage solutions are all about the tools and methods used to store, organize, and analyze the huge amounts of data produced by IoT devices. These solutions cover different storage setups like databases, data lakes, and cloud storage, tailored to manage the specific traits of IoT data, like its speed, size, and diversity. Moreover, IoT data storage solutions typically come with capabilities such as scalability, real-time processing, and security to address the varied needs of IoT applications in various industries.
IoT device management
When businesses incorporate IoT devices into their operations, they can choose to delegate the tasks of collecting, storing, and accessing data to external service providers. These providers often use specialized IoT software, which can be their own custom solutions or licensed platforms, to gather data from devices effectively. Additionally, they might provide extra services like data analysis, live monitoring, and predictive maintenance to enhance the efficiency and dependability of IoT implementations.
Cloud storages
The cloud storage system is widely adopted for IoT data due to its compact hardware requirements and minimal maintenance needs post-setup. With this approach, businesses can avoid the complexities of setting up and maintaining servers or additional equipment. It offers a hassle-free solution for storing and managing IoT data, enabling organizations to focus more on leveraging insights from their data rather than infrastructure management.
IoT analytics solution
Analytics applications extract valuable insights from IoT data, facilitating improved performance, enhanced security, and optimized energy efficiency. Beyond these benefits, they empower businesses to gain real-time insights into various aspects such as operating environment conditions, employee productivity levels, and financial metrics. By leveraging advanced analytics, companies can uncover trends, patterns, and anomalies within their IoT data, enabling informed decision-making and driving continuous improvement across their operations.
Hybrid cloud storing
Hybrid cloud systems can be likened to hybrid cars, as they offer the best of both worlds: internet connectivity for scalability and accessibility, combined with localized data storage and security. This unique combination ensures compliance with security standards and capacity needs, while optimizing performance and data privacy, enabling efficient compliance with regulatory demands.
Conclusion
Although IoT data storage brings exciting possibilities for innovation and productivity, it comes with notable security hurdles. Issues like unauthorized access, data breaches, malware threats, absence of encryption, and data interception can jeopardize the security and privacy of IoT data. Yet, taking proactive steps such as enforcing strong access controls, using encryption methods, deploying intrusion detection systems, and conducting routine security checks can help address these challenges and protect IoT data. By remaining alert and embracing thorough security measures, businesses can leverage the benefits of IoT technology while safeguarding their valuable data assets.





